One of the growing concerns with smartphones is security. My pocket-sized computer is more convenient and quicker at certain things than the laptop I carry around in my backpack; thus, I am prone to using it for many different tasks. In doing so, a lot of my personal information gets stored on the device. Among other things, pictures, addresses and bank information can be found with relative ease on my phone.
For most people, keeping this information safe is priority numero uno.
So the term "security" gets thrown around loosely and is often used as a scare factor to force users into believing everyone is out to get their information. It is also used as a marketing tool to convince consumers that one operating system is better and "more secure" than the next, or that you need premium mobile security software. By all means, you may. But companies tend to exaggerate to get you a little more interested and concerned with your own security when money is on the table. Their best marketing tool is fear.
While some operating systems – like BlackBerry OS, for instance, where RIM boasts security as a primary feature – are clearly more secure than others, the chances of that ever making a difference to the average end user are very slim. As long as you do your homework and stay on top of mobile news, your data and other private information will stay relatively safe.
That said, users' privacy on mobile devices has been tested as of late. As you may recall, it was discovered that the up-and-coming, mobile-only social network, Path, uploaded address books to their servers without users' consent. It was later revealed that Facebook and others were also being shady about their use of users' personal information. Once things like this go public, though, the guilty parties are usually all over themselves to right their wrong and calm the storm.
More so than other platforms, Android has been a target for malware and other info stealin' wares due to its relatively open system. Unlike Apple, whose App Store is rather tight on security, the Google Play Store does not have a rigorous approval process in place for application submissions. For iOS devices, this walled garden keeps out most – not all – of the muck. That said, Google does parse every application submission for known malware code. But the best way to try and keep your phone secure is to only install applications from trusted sources and trusted developers, and to carefully read the permissions before installing an application. (Trust me, that soundboard doesn't need access to your address book or your location.)
Last Monday, however, it was discovered – more or less, revealed – that Android applications do not require access to specific permissions to access private data. As a proof of concept, Paul Brodeur of Leviathan Security Group created an application, appropriately named No Permissions. Despite not being granted any system permissions, the application could still access all sorts of information and files stored on the SD card.
As The Verge pointed out on Friday, one of the more sensitive pieces of data that an application like that could target is photos. More specifically, the EXIF data from those photos and any geotagged information (i.e.: street addresses). Even with no permissions granted, applications can still send information to remote servers. Aaron Souppouris explains:
"No Permissions uses a simple but effective way to circumvent Android's data permissions. While the app itself is incapable of accessing the internet, it can launch Android's built-in browser to any page it choses [sic]. With the internet permission established via the browser, it could then send personal data to a remote location, although clearly the user would be aware that the browser was opened."
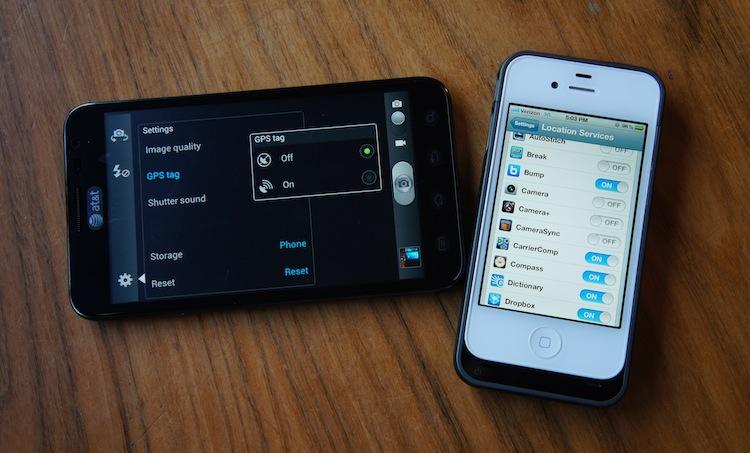
From your computer, it's not all that difficult to find an application that can access a photo's EXIF data. Earlier today, Jerry Hildenbrand of Android Central went in-depth on geotagging and EXIF data. Neither of these things are complicated or magical hidden features of your phone. Geotagging has been around for ages, and so has EXIF. But most people don't think of them as dangerous or a gaping security hole. Most probably don't take the time to understand what geotagging is before enabling it on their device. If you have location services or geotagging enabled when you're snapping photos, on any ol' phone (Android, iPhone, Windows Phone), your location is stored in that picture's EXIF data as longitudinal and latitudinal coordinates.
Essentially, creating an application that asks for no permissions, that can still access and make sense of EXIF data wouldn't be all that difficult – not for someone who knows what they're doing and what they're after. Sometimes, it's not even as difficult as that. If you share a photo with a geolocation to your favorite social network, all it would take for someone to find your house, place of business and routines is a little know-how and some time behind a computer.
While I can't speak for the other sites, Hildenbrand's piece was more of an insight to what exactly happens when you tag a photo with a location. It's a reminder of that time you just clicked "OK" for the "Do you want to share your location information?" prompt you skimmed over when you entered the camera application for the first time on your phone.
Point being, the next time you freak out over a story about a security risk for the mobile platform you use, remember all of those times you just skipped over all of the prompts and permission requests so you could dig into your phone or a new application a little quicker. Password or no password, security or no security software, your smartphone is only as secure as you allow it to be. Skimming over permissions and security prompts, and locally storing private information on your SD card is no better than installing blatant malware on you device.